The following is an excerpt from the Solution Guide: How to Improve Your Backup Data Security. Click here for free access to the full document.
Secure backups use a combination of implementation best practices and cybersecurity technologies. When using a software-defined backup solution, you typically have several decisions to make in how you arrange the infrastructure and operational workflow. The decisions you make will have an impact on business resilience, backup performance, security, complexity, and cost.
The 3-2-1 Backup Rule
Most backup vendors agree that the 3-2-1 rule is critical to maintaining data availability and mitigating the impact of cyber threats including ransomware.1 The rule indicates the following:
• 3 different copies of data
• 2 different types of media
• 1 of which is offsite
Here’s an example using Veeam, but any software-defined backup solutions can be configured in a similar way:
Determining Storage Media for the Offsite Copy
Although the idea is simple, the options for implementing this strategy are varied starting with the most critical decision: choosing the right storage media. When it comes to storing backups, there are generally 3 options for the type of repository: Local online media, offline media, and cloud. Each of those options can have advantages and disadvantages.
|
Storage Types |
Advantages |
Risks |
|
Online Media (SSD, HDD) |
• Greater control over your data • Faster performance • Readily accessible • Perform routine health checks |
• Networked media can be more easily compromised • Hardware failure and EOL upgrades • Offsite management and overhead • Can be costly to scale |
|
Offline Media (LTO Tape) |
• Can potentially be less expensive • Physical air-gap is more secure |
• Slower to restore in a disaster • Hardware failure • Offsite management and overhead • Limited health checks • Less accessible |
|
Cloud (Object Storage) |
• Makes the offsite copy fast and easy • Performance options • Affordable • Endlessly scalable • Multiple provider options |
• Less control over your data • Misconfiguration is a common risk • Cloud outages and downtime • Supply chain and backdoor exploits |
Applying Cybersecurity Controls
Secure backup repositories typically use one or a combination of the following cybersecurity controls. An ideal solution uses a combination of technologies, while also optimizing for performance, costs, and accessibility. It’s often ideal to find an existing, balanced vendor or solution to configure secure backup storage.
| Security Method |
How it protects data |
Concerns |
|
Encryption |
Encrypted backups are unreadable without the decryption keys, securing against theft attempts. |
Emerging attack vectors including steal-now-decrypt-later, compromised decryption key management and quantum computing undermine traditional encryption methods. Additionally, hackers using compromised administrator credentials can decrypt the data. |
|
Third-party Key Management |
Separating the encrypted data from the decryption key reduces the chance that threat actors will get access to both. |
Outsourcing to a third party may increase cost and complexity, and needs to be implemented correctly. |
|
Immutability (WORM) |
Immutable backups ensure that data in the repository cannot be altered for a period of time. |
Immutability alone does not protect data from exfiltration attacks, and can be circumvented via stolen privileged credentials or with some backdoor exploits. |
|
Multi-Factor Authentication |
Requiring additional methods of determining user identity to prevent unauthorized users from accessing data. |
Some software-defined backup solutions don't offer MFA protection before restoring or exfiltrating data, or the ability to add custom checkpoints. Additionally, insider threats or misconfiguration can result in data exposure. |
|
Physical Air-Gapping |
Air-gapped solutions restrict all wired access to the data repository including email clients, browsers, SSH and FTP. |
Failure points exist during data transfer through USB installers, exploits on remote code executions and trojans. Additionally, restore times from backup are long and the process can be expensive and cumbersome.
|
|
Logical Air-Gapping |
Creating a logical separation between the production environment and the backup repository adheres to zero-trust frameworks while maintaining overall data availability. |
Logical or virtual air-gapping is only as strong as the vulnerabilities affecting the storage itself, and the measures taken to avoid privileged credential compromise. |
Introducing the Data Harbor: Accessible Storage with Zero-Trust Controls
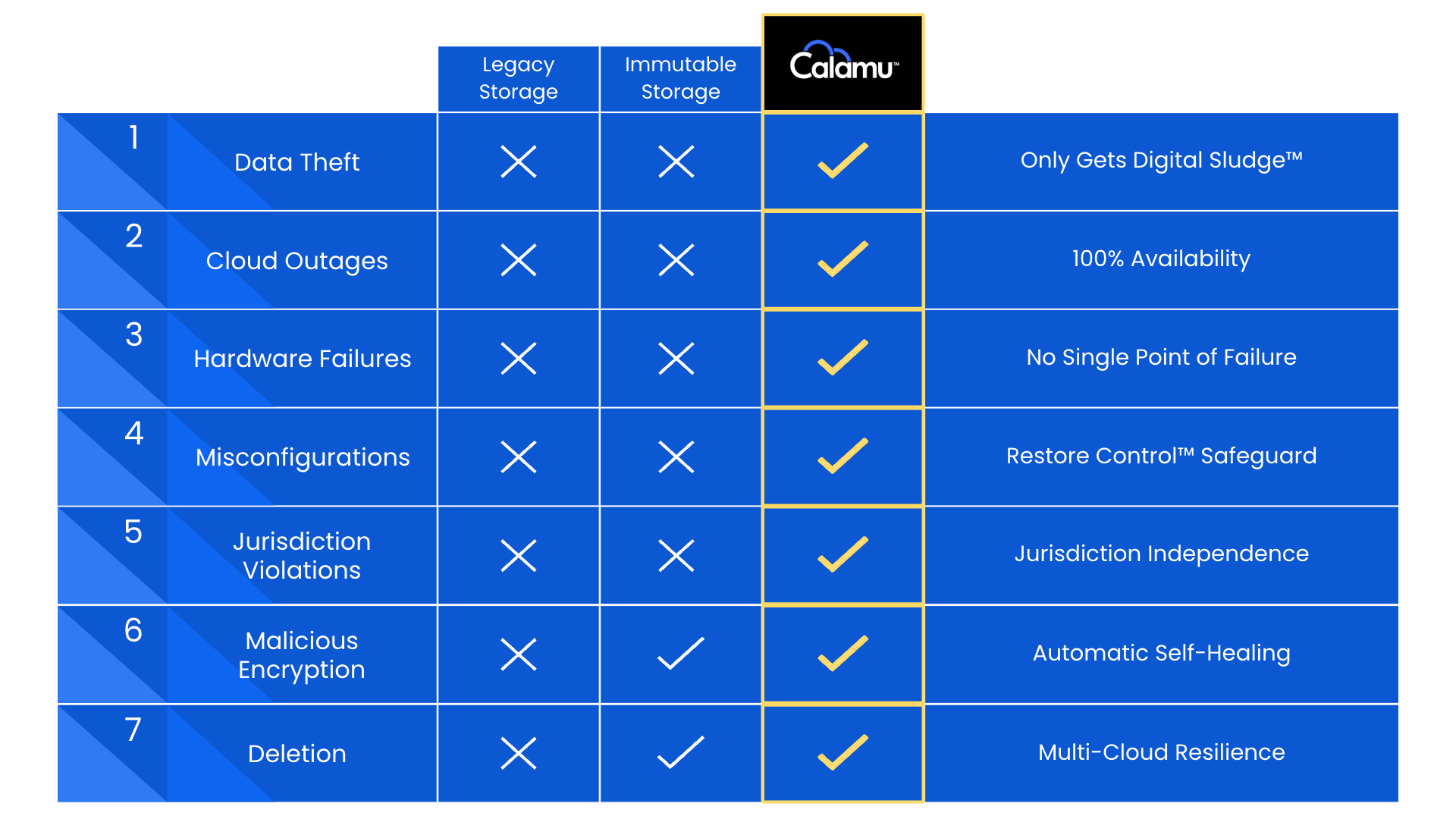
A Data Harbor is an approach to cloud storage that offers unique advantages and mitigates many of the risks. It functions just like any S3-Compatible object storage. However, instead of files being sent to a single cloud in their entirety, the file is fragmented across multiple clouds in a RAID type configuration with no single cloud storing a complete file or object. This architecture inherently removes any single point of failure.
Data is secure from theft and exfiltration, malicious encryption, deletion, or manipulation – all the tactics commonly used by ransomware actors. The data is also redundant across clouds, maintaining accessibility if one cloud experiences an outage or downtime.
Multi-Cloud Data Harbors combine physical security and cyber security, and are well suited to achieving 3-2-1 while also improving download speeds and backup performance.
Click below to download the full Solution Guide.