In Part I of this series, we discussed the emergence of the cyberstorage category, the need for data-first security that ensures protection against data theft and exfiltration, and the ways in which current systems fall short in addressing the double extortion ransomware trend. Now let’s take a look at what a cyberstorage solution entails and the benefits you can expect by implementing.
Cyberstorage Features
At its essence, cyberstorage combines security and proactive ransomware detection and response with accessible data storage. Cyberstorage solutions should be able to protect the data, even when perimeter defenses such as endpoint security or firewalls have been breached. Securing at the data level has become a focus in recent years as ransomware tactics shifted toward data theft for double extortion practices. As the category is set to grow by 6x over the next three years,1 let’s examine what a cyberstorage solution is and does:
Three Pillars to Increased Resiliency
Cyberstorage, according to Gartner, “protects storage system data against ransomware attacks through early detection and blocking of attacks, and aids in recovery through analytics to pinpoint when an attack started.”2 When evaluating a cyberstorage defense layer, companies need to consider the following:
- Built-in, proactive technology that can recognize anomalies and jump into action on their own by quarantining the threat location automatically, alerting and recording the activity for further investigation.
- Ability to recover and continue from an attack instantaneously, and self-heal the compromised data.
- Safeguards on the data-level that secure it against exposure, even if it has been exfiltrated during a breach.
Time is of the essence during a cyber attack. Cyberstorage solutions that integrate high-performing security analytics and intelligence with proactive triggers, based on the activity at the data level, can help reduce the speed to action and ultimately speed to recovery to boost the organization’s overall resiliency. It’s estimated that the fastest-moving ransomware can take over a system in less than 45 minutes.3 In addition, the average cyber attacker will lay in wait, undetected, for 11 days after breaching a network before deploying ransomware.4 Proactive detection means recognizing the attack and stopping it in its tracks by quarantining the threat location automatically. It also means alerting and recording the activity for further investigation as well as safeguarding the data even if it is accessed.
How Cyberstorage Works
Cyberstorage offers a data-first security approach with the goal to withstand a ransomware attack and eliminate the impact of a breach. In transforming how data is stored, cyberstorage solutions ensure that data remains accessible on a daily basis for normal business activity while also adding security layers onto the data itself. There are a number of methodologies that have emerged as the category has grown, below we will discuss how Calamu approaches cyberstorage:
The following is an excerpt from Securing Data From the Inside-Out; A Master Guide to Understanding Modern Data Threats.
Understanding Modern Data Threats.
Step 1: Secure the data by removing value to unauthorized users
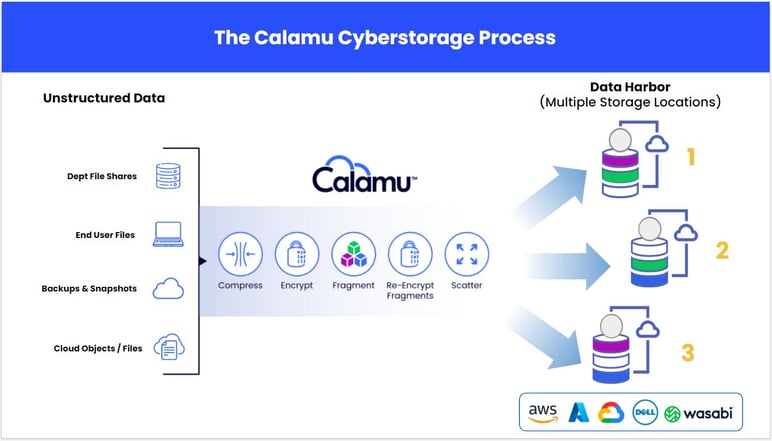
Calamu Protect first runs data through a multi-step process that compresses, encrypts, breaks data into fragmented pieces, and then re-encrypts those pieces using different keys. The technology that enables this process never reads the data itself but instead works through the metadata, eliminating the threat of a third-party failure point. Next, the fragments are dispersed geographically across multiple cloud or local storage locations. The process of scattering the fragments ensures that no single location has all the fragments required to reconstitute the data (and that is assuming each fragment was decrypted against its own key before reassembly). Additionally, the fragments that comprise a data object or file are not all stored in the same cloud provider, nor are they all stored in the same geographic region. So, the data no longer exists to anyone but you, the rightful owner. No single cloud provider and no single geographic region has enough of the fragments to reconstitute the file.
Step 2: Ensure Accessibility and Performance through a Data Harbor
The result of the above described process is a virtual data harbor, a neutral environment that holds the knowledge to piece the fragments back together instantaneously for an authorized user to work on before scattering the encrypted fragments back to their disparate locations. The fragments in a data harbor are immutable—meaning changes to the source data are versioned and fragments cannot be removed outside of the file versioning system itself. Therefore, stolen credentials are useless for attempts to encrypt and destroy data. However, data accessibility means nothing without speed of access. The architecture of a data harbor was engineered with performance in mind. Tests show that it is 56% faster in most cases using a 100MB file size compared to a direct cloud upload or download.
Step 3: Absorb the Attack and Eliminate Downtime
The data harbor is built to detect an event as it occurs and self-heal instantaneously. Should an errant process, bad actor, or stolen service credentials offer unauthorized access where a fragment is modified or removed, the location immediately becomes quarantined, and the data harbor rebalances to new secure storage locations. This means that even if a breach occurs, the attack is absorbed by self-healing, and business operations continue without any downtime.
Benefits of Cyberstorage
- Unprecedented security against data theft and exfiltration to guard against multi-faceted ransomware extortion attacks
- Secure file sharing and transfers
- Automatic breach detection and self-healing that absorbs the attack and eliminates downtime
- Granular details and control over data storage and access for increased efficiency
Learn more about cyberstorage. Jump to Part I to learn more about the key market drivers behind the category and Part III to see how to implement, where cyberstorage fits in your existing architecture and answer many common questions.




